What is Cyber Cube?
In today's reality of lack of talent and a flood of security products, many companies are looking for the right solutions to build structured defense methods.
Cyber cube is a self-use service that provides a quick overview on your organizational posture and readiness for an APT (Advanced Persistent Threat) attack.
It will take you through the "cyber kill chain" with a detailed questionnaire about the 3 main defense vectors.
At the end of the process you will receive a picture of your organization's vulnerabilities and breaches (from the attacker's point of view) that can help you with more efficient protection.
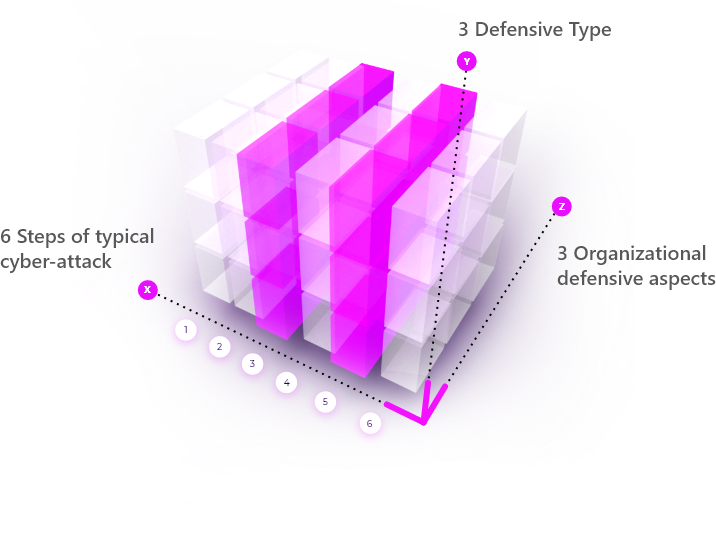

Main three organizational defensive aspects (Z axis):
1 Preventive
Prevention is the first line of the defense in the control structure. Preventive is a passive technique designed to reduce the frequency of occurrence of undesirable events.
2 Detective
The second line of defense. These are devices, techniques ,and procedures designed to identify and expose undesirable events that elude preventive controls.
3 Responsive
The third line of defense. In order to limit the impact of an incident, Finding the root cause of the incident, Permitting affected systems back into the production environment and ensur that no threats are remains.
Six steps of typical cyber-attack (X axis)
Reconnaissance
Refers to the preparatory phase where an attacker seeks to gather information about the target prior to launching an attack. The attacker can choose or combine between passive reconnaissance (without directly interacting with the target) or active reconnaissance (interacting with the target directly by any means).
Getting Access
The attacker penetrates and obtains an initial hold on the victim's systems and network by activating the most targeted and effective "weapon" type to exploit the vulnerabilities identified in the Reconnaissance phase (zero-day break, social engineering, phishing, hacking, etc.).
Maintaining Access
The attacker penetrates and obtains an initial hold on the victim's systems and network by activating the most targeted and effective "weapon" type to exploit the vulnerabilities identified in the Reconnaissance phase (zero-day break, social engineering, phishing, hacking, etc.).
Lateral Movement
Once an attacker has established an hold based on the victim's internal network, he/she can now deepen its lateral movement on the network by installing malwares and gaining control over organizational assets. As part of this step, the attacker actually "lives on the victim's network", studies the him and prepares the infrastructure required to carry out the attack.
Preforming The Attack
At this step, the attacker executes his ultimate goal and implements the attack (theft of information, deletion of data, disabling of core systems, loading of network activity, damage to organizational assets, etc.).
Covering Tracks
The attacker uses various techniques and tools (Log Cleanup etc.) to hide and disguise his traces on the network to hinder the investigation process.































